Understanding Public and Private Keys and Consensus Protocol
This Blog comprises of the transaction working in the Blockchain Wallet.
Introduction:
Blockchain technology is built upon a foundation of cryptographic principles that ensure security and trust within the network. Two crucial components of this security are public and private keys. In this blog post, we'll explore what public and private keys are, how they work, and their significance in the world of blockchain.
Public and Private Keys: The Basics
At the heart of blockchain technology, there is a fundamental concept: asymmetric cryptography. It uses a pair of keys - a public key and a private key - to secure transactions and data on the blockchain. Let's dive into these keys individually.
Public Keys
A public key is, as the name suggests, public. It's an address or identifier that anyone can see and use to send you cryptocurrency or verify your digital signature. It's like your bank account number, a public identifier that allows others to interact with your account.
Private keys
On the other hand, a private key is a closely guarded secret. It's a long, random sequence of characters that is used to sign transactions, proving that you have control over the associated funds. Losing your private key is akin to losing your access to your bank account.
How Public and Private Keys Work Together
Suppose, we have to send a transaction to another person. You know that, in the blockchain, there is no central authority to check whether the transaction is correct or not. So here, we have a private key which is a secret key to do transactions from us.
From this private key, a public key is generated, which can be viewed by anyone. This key tells us that the transaction is done by us.
At this stage, the receiver only knows that a transaction is received in the name of us.But, it doesn't mean that it is done by us. So to verify that, a signature is created which is a combination of our message or transaction and private key.
To ensure that the transaction done from us is correct or not, a miner has a verification function that inputs the transaction, signature and private key. If the answer is yes, then the transaction gets accepted and validated. If not, it will not get accepted.
We can understand this through a diagram:
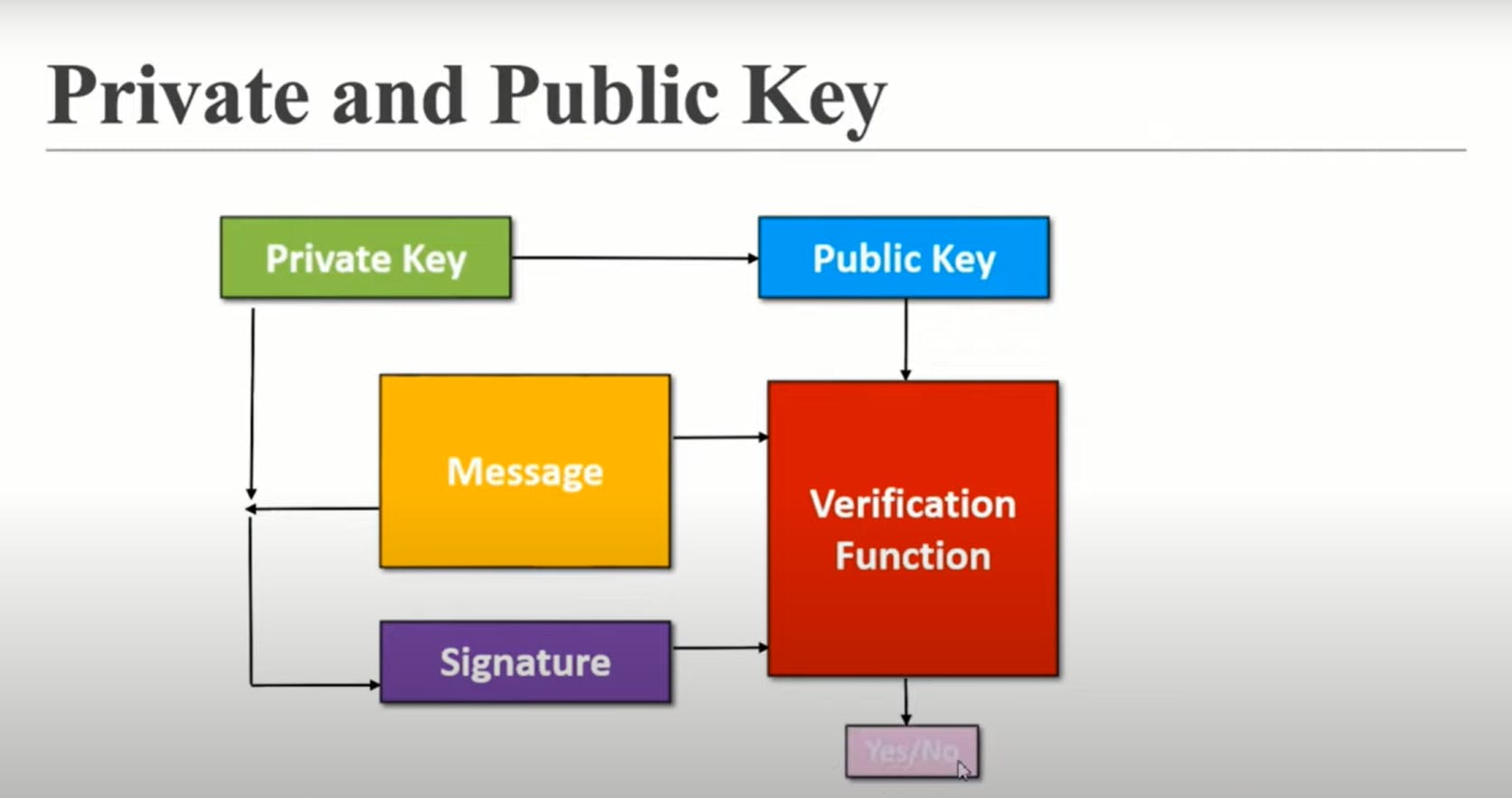
To summarize this:
When you want to send cryptocurrency or sign a transaction on the blockchain:
You use your private key to create a digital signature for the transaction.
The transaction, along with the digital signature, is broadcast to the network.
A verification function is used to verify the transaction, signature and public key
to add it to the blockchain.
Others can use your public key to verify the digital signature and confirm that it indeed came from the rightful owner of the private key.
This process ensures that only the owner of the private key can authorize transactions. It's the foundation of trust in blockchain networks.
Consensus Protocols
Now that we've covered public and private keys let's delve into the concept of consensus protocols, which are critical in maintaining the integrity of the blockchain.
Types of Consensus Protocols:
There are several consensus protocols, each with its unique way of achieving agreement. Let's look at two prominent ones:
1. Proof of Work (PoW)
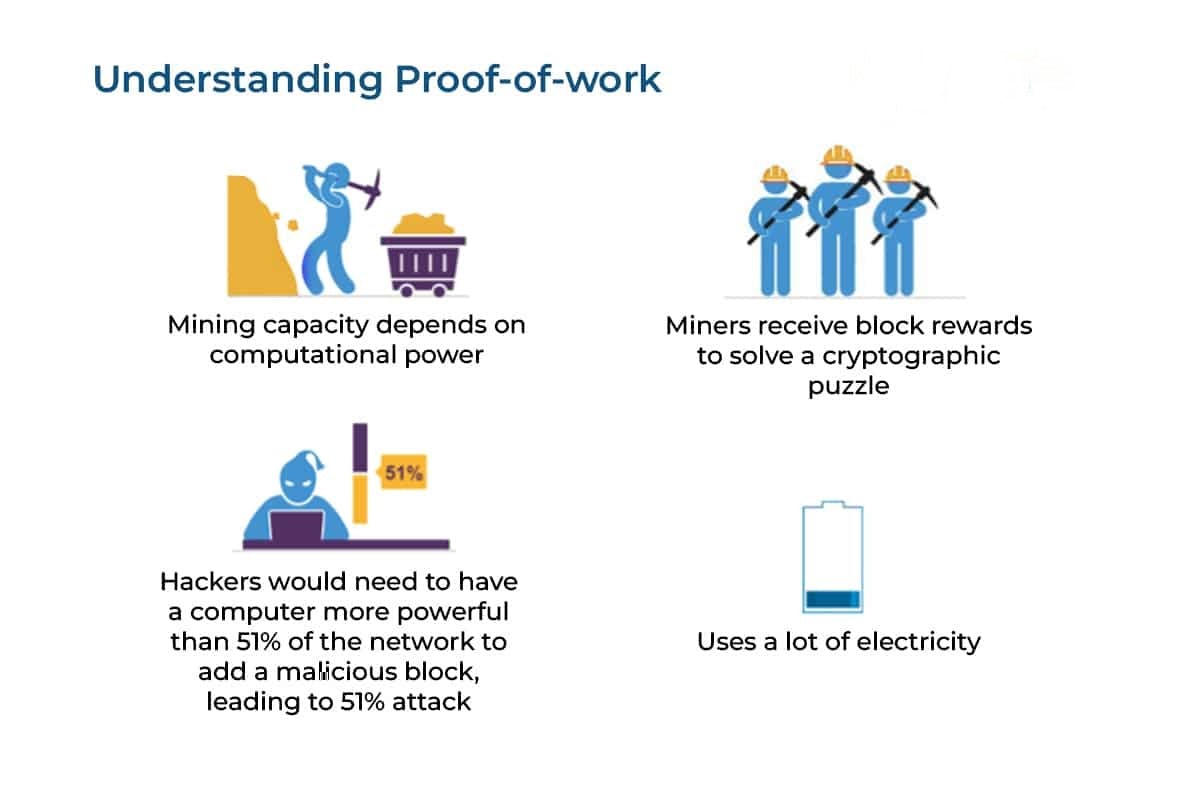
Proof of Work is the original consensus algorithm used in Bitcoin. Miners compete to solve complex mathematical puzzles, and the first one to solve them gets the right to add a new block to the blockchain. It's energy-intensive but has been proven to be highly secure.
2. Proof of Stake (PoS)

Proof of Stake is an alternative to PoW, where validators are chosen to create new blocks based on the amount of cryptocurrency they "stake" or lock up as collateral. This reduces energy consumption but still maintains security.
Proof of Work Vs Proof of Stake
I will provide a diagram so that you understand in a better way:

Conclusion:
Public and private keys are the bedrock of blockchain security, ensuring that only authorized individuals can access and transact on the blockchain. Consensus protocols, on the other hand, maintain the network's integrity and trust by enabling participants to agree on the state of the ledger.
Understanding these concepts is crucial for anyone interested in the world of blockchain, as they are at the core of its functionality and security.
Remember, while public keys are open for everyone to see, private keys should always remain a closely guarded secret to protect your digital assets. And the various consensus protocols ensure that everyone in the network plays by the same rules, ultimately upholding the trust and reliability of blockchain technology.
See you all in the next blog. Stay tuned to our blog series.
